Below is an article published by Cyber Citadel’s Lead Security Researcher Rafay Baloch on the technical comparisons between Signal and Telegram messaging services. By Rafay Baloch.
Facebook had long aspired to integrate WhatsApp data with Facebook, Instagram and Messenger’s back ends for better ad targeting and data monetization. As a trade-off, WhatsApp has decided to lose several million users in pursuit of its lucrative commercial prospects. Clearly, this seems to be the new direction for Whatsapp contrary to the early claims of keeping it ad-free. Whatsapp recently released its new privacy policy which describes “Key Updates” on the way user data will be processed. Whatsapp has clarified that the new privacy changes only affect how users interact with Whatsapp businesses accounts which will be shared with Facebook’s network for displaying targeted advertisements. This new policy is being rolled out on 8 February 2021 and users are forced to either accept the terms or delete their WhatsApp accounts. This has triggered a debate on social media platforms discussing suitable alternatives. As a result, Telegram and Signal have seen a huge surge in demand and adaptation. While I have highlighted key security differences between Signal and Whatsapp, there is an on-going debate on which is better from a privacy and security standpoint. Therefore, I decided to shed some light on key technical differences between Signal and Telegram.
Signal and Telegram: Secure by Default
First and foremost, in security, we rely upon technologies that are secure by default. Both, Signal and Telegram support end-to-end encryption (E2E). However, Signal has E2E enabled by default, whereas Telegram requires a secret chat to enable E2E on a conversation to conversation basis. This makes Telegram’s default conversations even less secure than WhatsApp as E2E is applied by default on WhatsApp for all conversations. Telegram describes this lack of default encryption as “convenience”, as Telegram’s normal conversations are encrypted when stored in the cloud and can be synced across multiple devices. Their secret chats, have to be backed up manually.
Group chats for Signal are encrypted with E2E encryption by using Multi-party Off-the-Record Messaging (mpOTR). Whereas group chats for Telegram are not encrypted.
Signal and Telegram: Data Storage
By default, Telegram chats are stored in the cloud unless secret chat is enabled. Telegram claims to have data stored across distributed infrastructure, with it’s cloud data heavily encrypted. The security key is distributed across different jurisdictions to prevent information disclosure from one country to another, or a small groups of allies that request for the data or encryption key.
There are still a couple of problems with this approach. Since the encryption keys are stored on the server, Telegram can decrypt conversations stored on its cloud. Secondly, in the event of a compromise of Telegram’s infrastructure, an adversary can obtain security keys to decrypt conversations. The popularity of Telegram, especially in authoritarian regimes, makes Telegram a lucrative target for nation states. Therefore, the entire security model of Telegram’s cloud relies upon trust in a centralized authority, which from a security standpoint is a flawed approach.
Signal on the other hand stores messages in a local SQLite database once they are decrypted. The local database is encrypted with SQLCipher.
Signal and Telegram: Collection of metadata
Telegram’s privacy policy states that, as a part of their spam and abuse prevention procedure, they collect information such as IP addresses, device details, history of username changes, and more. This data, if collected, is stored for a span of 12 months before being deleted.
On the flip side, due to a lack of data monetization, Signal collects minimal metadata, which is only required to effectively deliver its service. This is evident from the subponea received by Signal from the Eastern District of Virginia to provide details about two Signal numbers. The data provided in response was the timestamp of account creation and the last time the user connected to the Signal server limited to the day instead of an hour and a second.

Contact Discovery
For all messaging applications to build a social graph, user’s contacts must be present on the same messaging application. For this purpose, they use the device address book to query numbers in the contact registered under the same service.
In Telegram, the entire address book is uploaded to the Telegram cloud, where it’s stored to notify if anyone from the contact list signs up for Telegram’s service. This way Telegram learns about your social graph, including people who don’t use their service. The very same method is deployed by Whatsapp.
Signal does not learn about your social graph, as it uses Intel’s SGX (Software Guard Extensions) for contact discovery. SGX allows application software to be stored in a protected software container referred to as an enclave. SGX enclave is ideal for scenarios where the client or server does not need to learn about the contents of the program execution. To make sure that applications running under SGX enclave are not tampered with, SGX supports a method known as remote attestation to verify integrity.
Signal runs their contact discovery service under a secure enclave on a Signal server, whereby the secure enclave learns about contacts as a part of their discovery and transmits it back to a client as encrypted. Since enclave uses hardware-based memory encryption, the operating system is unable to read the contents of the memory. This means that even if an adversary manages to compromise Signal servers, they would be unable to retrieve address book contents because the content memory would be encrypted. Signal has gone a step further to prevent OS from learning about memory access patterns. Signal has written a detailed article about it here. Matthew Green, a prominent cryptography expert, has criticized the reliance on SGX and specifically SGX remote attestation process.
Source Code
Open-source offers a wide variety of advantages in terms of security, the most important being greater transparency and very basis of trust. Signal’s entire source code for all its client-side applications, as well as servers, are open-source for anyone to examine the presence of backdoors and security vulnerabilities.
Telegram is partially open-source. The client-side applications of Telegram are open-source, whereas the server-side of Telegram is closed source on writing.
Encryption Protocol
Signal uses its own protocol for delivery of E2E. Signal’s protocol has been adapted by Whatsapp, Facebook Messenger, Skype and many other messaging service. Signal’s protocol is built on well known, tried and tested security standards. The protocol has gone under extensive review, audits and scrutiny by the security community and cryptography experts. In the paper “A Formal Security Analysis of the Signal Messaging Protocol“, after performing an in-depth security analysis of Signal’s protocol, researchers concluded that it was sound from a cryptographic standpoint. The research involved analysis of Signal’s core security properties against the researcher’s propriety security model, which they describe as ‘comprehensive’.
Similarly, the prominent cryptography expert Matthew Green has endorsed Signal’s novel implementation of future secrecy. Signal does this by using a novel technique known as ratcheting, which uses a new session key for every new message. This means that, in the case of a compromise of the session key, an eavesdropper will not be able to decrypt future communications.
Telegram on the other hand, has been criticized by cryptography experts for using a non-standard cryptographic protocol known as MTProto. All algorithms were designed by someone at a certain point. However, trust cannot be achieved unless the scheme has gone through years of in-depth analysis, rigorous testing and extensive scrutiny, which is not the case with MTProto.
Several security flaws have been discovered in MTProto, however most of them have been theoretical in nature. Despite criticism, Electronic Frontier Foundation’s secure messaging scorecard has rated Telegram’s secret chat 7/7. Similarly, in the white paper “Automated Symbolic Verification of Telegram’s MTProto 2.0”, researchers confirmed the protocol being sound, saying, “In the light of these results, we can affirm that MTProto 2.0 does not present any logical flaw.” However, they did discuss the possibility of implementation flaws and side-channel attacks.
Compliance with Legal Requests
Telegram, unlike Signal, has public channels that can be used to broadcast messages to a wide number of subscribers. Like any other social platform, these public channels have been subject to misuse and have been used to spread disinformation/propaganda and coordinate protests, and have therefore faced increased pressure. Telegram has a history of compliance with Iran and the Russian government. For instance in 2017, Telegram shut down the channel of the Iranian opposition for inciting violence at the government’s request. Similarly, Telegram agreed to restrict certain bots and stickers in Iran.
Telegram was also banned in Russia from April 2020 due to non-compliance with the FSB to grant an encryption key. The ban was lifted in June 2020 upon agreement that Telegram assist in the investigation where required. Although, Telegram has confirmed in it’s privacy policy that it is yet to record a single case of data disclosure at the request of any government. Clearly, given the history of compliance requests, this statement certainly raises skepticism.
As discussed earlier, since Telegram collects and stores a wealth of metadata for its service delivery, the data could be of great interest to a government, and Telegram would be compelled to give details under court order. Regardless of the claims about keys being in a different jurisdictions and hence requiring court orders from multiple jurisdictions to comply with a request, the underlying problem here is trust in the service to keep your secrets. The following tweet by “Edward Snowden” summarizes the argument.
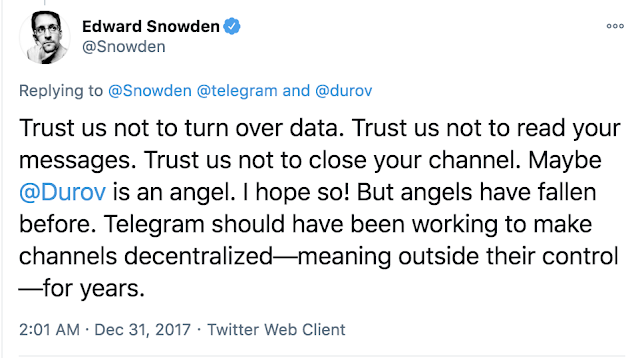
Signal, on the other hand, is in the process of adopting a zero knowledge system and stores minimal data. The data is of no value to any government even if Signal were compelled to release it under court orders.
View Cyber Citadel’s full video library on our YouTube channel



