During a red team exercise for a global logistics provider, Cyber Citadel security researchers Rafay Baloch, Hammad Shamsi and Muhammad Samak found a directory traversal vulnerability affecting QNAP devices running QTS.

After reproducing and verifying the directory traversal (a.k.a path traversal) vulnerability in April, Cyber Citadel researchers followed responsible disclosure policies, notified QNAP of the vulnerability and granted a 60-day time frame for QNAP to issue a patch before publicly disclosing the weakness as per Cyber Citadel’s responsible disclosure policy.
Directory traversal allows an attacker to access restricted directories and files, and allows an attacker to execute commands outside of the server’s root directory. This attack can be broadly classified under access control flaws. This vulnerability occurs, for example, when a page receives, as input, the path to the file that must be included and this input is not properly sanitised, allowing directory traversal characters (such as dot-dot-slash) to be injected.[1]
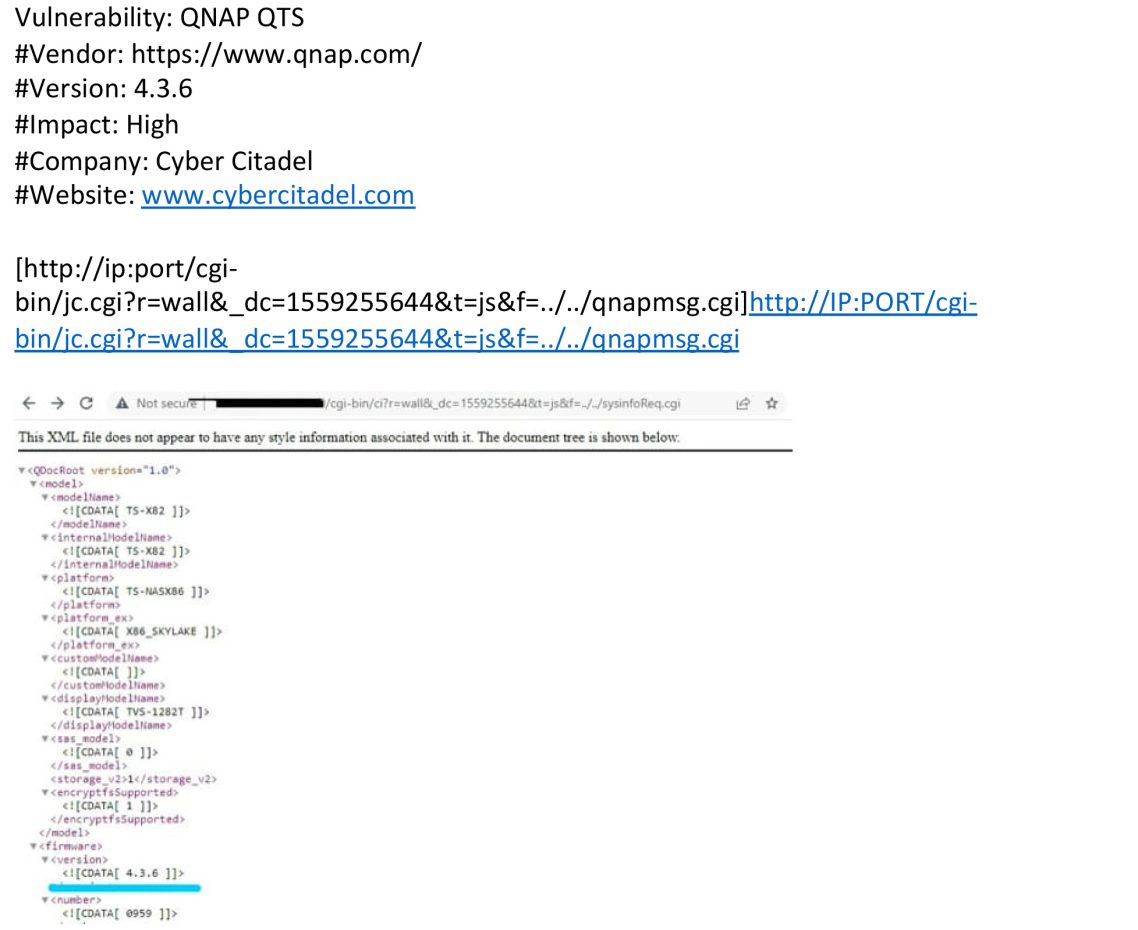
In the case of QNAP’s QTS system, the directory traversal vulnerability would have allowed remote attackers to retrieve arbitrary files via the “f” parameter. By providing a specially crafted path to the vulnerable parameter, a remote attacker could have retrieved the contents of sensitive files on the local system.
POC for Directory Traversal Vulnerability
Vendor Response
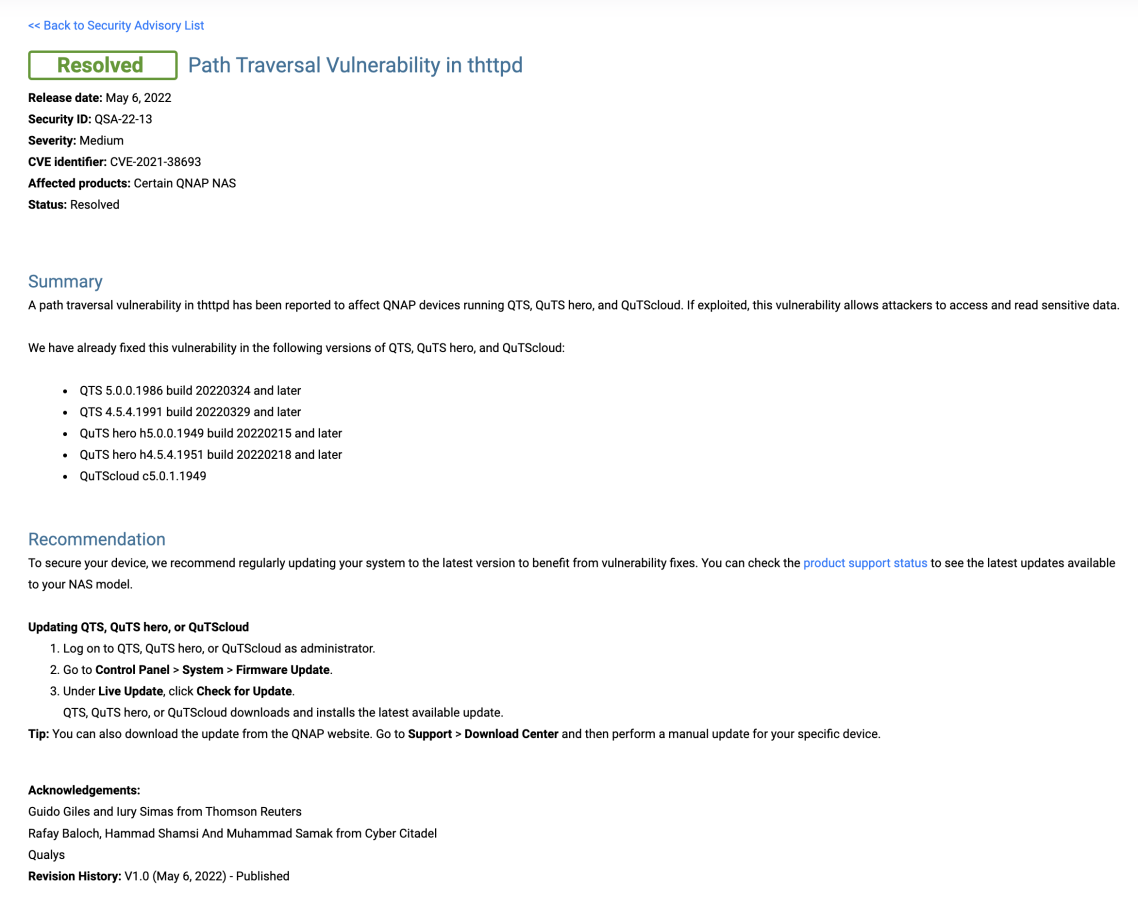
QNAP disclosed the path traversal in thttpd on 6 May 2022, citing the vulnerability as affecting QNAP devices running QTS, QuTS hero, and QuTScloud and describing it as allowing attackers to access and read sensitive data.
During discussions with the vendor, QNAP revealed the vulnerability had also been found by Manager Broadcast TV Support Guido Giles and Lead Information Security Analyst Iury Simas from Thomson Reuters in February this year. QNAP credited all parties for finding the vulnerability in their disclosure release.
QNAP recommended that customers update their systems to the latest versions to benefit from the patches, as well as directions on how to do so.[2]
Impact
Although QNAP assigned the vulnerability as medium severity in their disclosure, Cyber Citadel considers directory traversal as a critical vulnerability with a severe impact and a high likelihood of exploitation.
The impact can vary based on the level of exploitation and the read permission of the webserver user. Depending on these factors, an attacker might carry out one or more of the following attacks:
- Gather usernames via an “etc/passwd” file
- Harvest useful information from the log files, such as Apache logs/access files
- or, remotely execute commands by combining this vulnerability with other attack vectors, such as a file upload vulnerability or log injection.
Mitre’s list of CWEs gives directory traversal a high likelihood of being exploited if left unattended, citing examples where attackers could gain access to passwords, logs and system files.[3]
Cyber Citadel Recommendations to Avoid Directory Traversal
- If possible, do not permit appending file paths directly. Make them hard-coded or selectable from a limited hard-coded path list via an index variable.
- If you absolutely need dynamic path concatenation, ensure you only accept required characters such as “a-Z0-9” and do not allow “..” or “/” or “%00” (null byte) or any other similar unexpected characters.
- It is important to limit the API to allow inclusion only from a directory and directories below it. This way you can ensure any potential attack will not perform a directory traversal attack.



