Below is an excerpt from the article “Address bar flaw and big rise in spear-phishing shows why better defences are needed against Covid-19 cyber attacks” as published in the South China Morning Post (scmp.com). By James Springer
Cybercriminals increased their rates of spear-phishing attacks by 667 per cent this year due to Covid-19 and online dependency, according to IT security company Barracuda Networks.
Spear-phishing is a common online fraud whereby emails are sent from a known or trusted sender to induce targeted individuals to reveal confidential information.
Coronavirus-themed malicious emails and fraudulent websites are tapping new trends in online shopping, communication and remote work by taking advantage of what is top-of-mind for end users and their online search patterns.
Jonathan Sharrock, CEO at cybersecurity firm Cyber Citadel, has seen first-hand the increasing trouble experienced by organisations from spear-phishing attacks.
“Spear-phishing is sophisticated in a lot of cases,” said Sharrock. “The individual or organisation is well researched and the chance of success is often extremely high. Some of our simulated campaigns where we craft rather compelling phishing emails show that employees … will click on a link embedded in an email, if it looks convincing enough.”
A mobile web browser vulnerability recently disclosed by Rafay Baloch, lead security researcher at Cyber Citadel and Tod Beardsley, director of research at Rapid7, reveals how spear-phishing has gained a sharper edge.
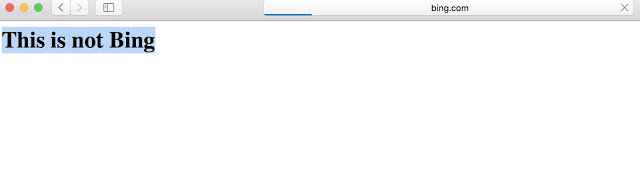
The previously undiscovered flaw potentially allows attackers to host malicious websites imitating legitimate services, while going undetected by standard mobile web browser address bar security protocols. The affected web browsing applications include Safari, Opera, Yandex, UC Browser, Bolt and RITS – across both Android and iOS platforms.
Baloch found the address bar flaw earlier this year and along with Beardsley reported it to the relevant vendors on August 10, 2020. After allowing the standard industry practice of 60 to 90 days for vendors to issue a patch, they released the public disclosure on October 20.
“Spear-phishing attacks have been on a massive uprise since the inception of Covid-19,” says Baloch. “So employees are being targeted by spear-phishing whereby attackers are registering domains with key words such as ‘Covid-19’, ‘Wuhan,’ ‘vaccine’ – to entice and persuade the victim into clicking on links.”
Despite the heightened risk, Apple, Opera and Yandex were the only vendors to respond with fix dates in under 60 days. Apple responded with a fix released on September 16, and Yandex published a fix on October 1.
Opera fixed the vulnerability in a software update released on September 15. “Security issues regarding spoofing get high priority within Opera,” said Alejandro Viquez, senior communications manager at Opera.
Other vendors mentioned in the disclosure, however, were slower to respond.Although less popular than Safari and Opera, they have user bases that cannot be ignored in terms of size and scope. UC Browser, largely used on Android devices in China, India and Indonesia, currently logs over 500 million users on Google Play. Although Bolt and RITS have significantly lower user figures, they are used specifically for reasons of data security.
Darryl Chander from Advo Indonesia, a public relations agency representative for UC Browser, said on October 21 that “UC Browser available on Google Play Store complies with its stated app policies. We will reach out to the regarded two researchers as soon as possible to confirm our effort to resolve this issue.”
“We missed his first mail,” said K. A. M. Rashedul Mazid, managing director of RITS. “Later when we found it, we contacted them for more information about it.” RITS are due to release an update next week.
Bolt’s support e-mail from Rapid7 bounced. They could not be reached for comment.
“In the end, if you can get people to believe that your password-stealing website is in fact ‘google.com,’ or some other household name, that‘s a pretty solid attack that will have a better chance of being successful,” said Beardsley.

The coordinated disclosure seriously questions the inherent faith in mobile URL security certificates, thought to be the best way end users can ensure a website’s legitimacy. It is also a crucial example of the responsibility major software developers have to keep their products secure at a time of heightened cybersecurity awareness.
“If you look at the Google Vulnerability Reward Program’s official page, they have clearly and categorically stated that the address bar is the only reliable security indicator in modern browsers,” says Baloch.
“Imagine a scenario where you are browsing any domain of your choice, and the address bar says its Google.com, or WHO.org, but the content is being controlled by an attacker. There is absolutely no way for a common user to know whether the domain is legitimate or not. This is what an address bar spoofing vulnerability exploits in a browser.”
| CVE | Vendor | Browser | Version | Platform | Fixed? |
|---|---|---|---|---|---|
| CVE-2020-7363 | UCWeb | UC Browser | 13.0.8 | Android | Fixed v13.3.2 on Oct 21, 2020 |
| CVE-2020-7364 | UCWeb | UC Browser | 13.0.8 | Android | Fixed v13.3.2 on Oct 21, 2020 |
| CVE TBD-Opera | Opera | Opera Mini | 51.0.2254 | Android | Fix expected from vendor Nov. 11, 2020 |
| CVE TBD-Opera | Opera | Opera Touch | 2.4.4 | iOS | Fixed in version 2.4.5 released Sep 15, 2020 |
| CVE TBD-Opera | Opera | Opera Touch | 2.4.4 | iOS | Fixed in version 2.4.5 released Sep 15, 2020 |
| CVE TBD-Opera | Opera | Opera Touch | 2.4.4 | iOS | Fixed in version 2.4.5 released Sep 15, 2020 |
| CVE-2020-7369 | Yandex | Yandex Browser | 20.8 | Android | Automated reply, followed up Oct. 19, 2020. Fix published Oct 1 in version 20.8.4. |
| CVE-2020-7370 | Danyil Vasilenko | Bolt Browser | 1.4 | iOS | Support email bounced, alerted Apple product security |
| CVE-2020-7371 | Raise IT Solutions | RITS Browser | 3.3.9 | Android | Fix expected Oct. 19, 2020 |
| CVE-2020-9987 | Apple | Safari | iOS 13.6 | iOS | Fix released Sept. 16, 2020 |
Not only a boon for social engineering scammers, this so far underappreciated address bar vulnerability also has the potential to bypass common automated security solutions put in place by companies and organisations.
“A lot of anti-phishing tools basically look for suspicious domains,” says Baloch. “But in the case of address bar spoofing, there is no way for anti-phishing tools to realise it, because it’s the browser that creates the illusion that the domain is an authentic website.”
“I believe address bar spoofing is going to be used more and more in the future because it gives an advantage to the attacker,” says Baloch. “Considering that spear-phishing is the most exploited vulnerability during Covid-19 … this vulnerability should be considered high risk instead of medium risk.”
October is recognised by many countries around the world as National Cybersecurity Awareness Month, spurred by the cyberattacks code-named Titan Rain that targeted several US government agencies in 2003. However, many people and organisations remain unaware of the dangers to personal and corporate data from weak cybersecurity defences.
“For the browser vendors that didn‘t respond to our disclosure with a patch within the 60-day disclosure period, I’m hopeful that this is the nudge they need to get into the coordinated vulnerability disclosure game,” said Beardsley.
Full article published in the South China Morning Post (scmp.com) – 24 October 2020, “Address bar flaw and big rise in spear-phishing shows why better defences are needed against Covid-19 cyber attacks”.



