Imagine you’re buying a business. The first step would, of course, be to carry out financial audit to help assess the risk and return profile of the business. You will need to know its current financial position, establish the value of its assets, and make sure it will be stable and viable in the future.
The last thing you want to do is acquire a business and subsequently discover it has cooked books, unpaid debts, unresolved litigation, a case of money laundering, and fines from the state revenue and customs department.
Imagine a scenario where you don’t bother with a financial audit and just take an unknown risk. Of course, you can’t. So why would you do that with cyber security risks?
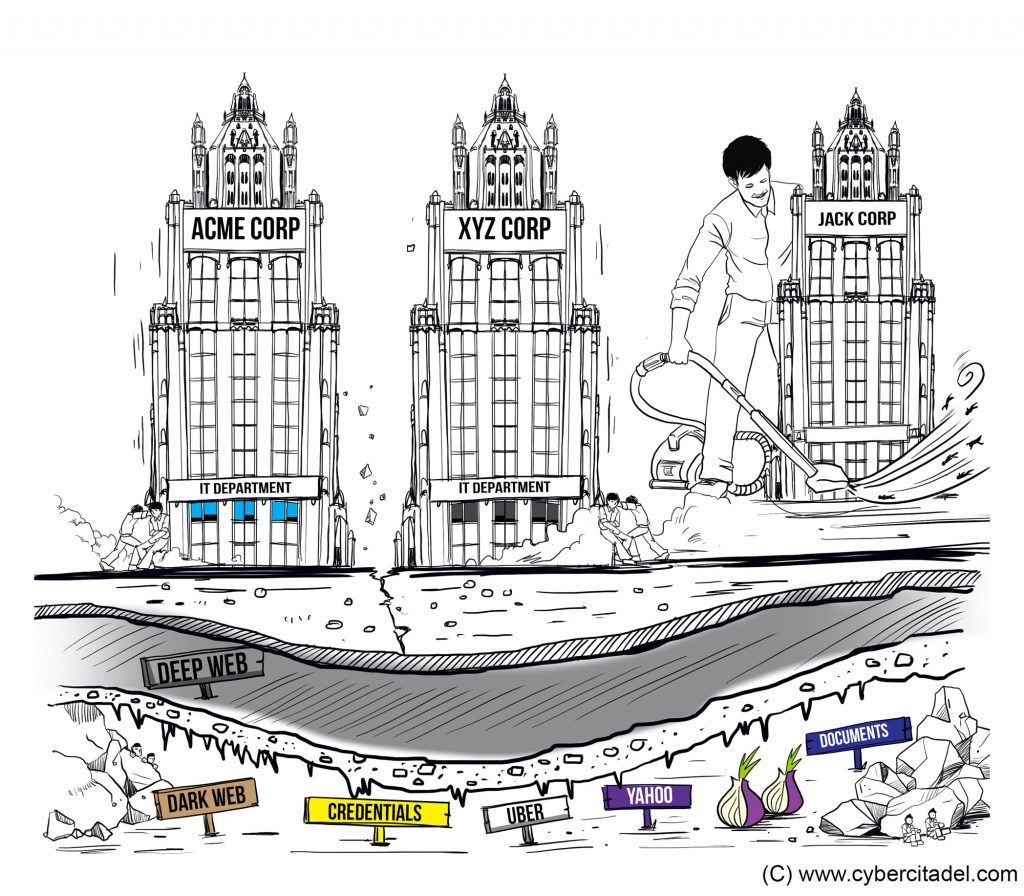
In the technology age, the digital footprint of a company is just as important as its financial one and might even result in greater loss in value. The selling price of Yahoo! dropped by US$350 million when it was revealed to buyer Verizon that 1.5 billion user accounts had been compromised within months of the deal.
Two broad categories define potential risk – historical cybersecurity issues, and present digital infrastructure. Historical cybersecurity encompasses previous instances of cyber-attack, known cases of data loss, and previous counts of non-compliance with data and cybersecurity regulations.
The state of present infrastructure may be considerably less obvious but is potentially more important. You need to know if their infrastructure is compliant with regulation now, if there has been any theft of data or intellectual property (IP), and if this has been recovered.
If not, that business could be at risk of public embarrassment, bribery or blackmail, or losing key products to competitors, all of which drive up uncertainty and bring down company value.
At the very least, it may cost an acquirer in future fines or litigation. Last year, discount taxi company Uber paid US$148 million to settle legal action involving a cybersecurity attack exposing millions of customers’ data back in 2016, which they hid from regulators.
If Uber had been acquired during this time, the acquirer may have been liable if this security breach not been flagged during the due audit process.
It is important to realise that this issue affects everyone, though maybe in different ways. Companies that handle personal data may have a high risk of data loss, but logistic firms might have a greater risk of network destruction, and research and development (R&D) companies at a greater risk of bribery or ransom from IP theft.
According to professional services firm PricewaterhouseCoopers, 80 percent of global deal-makers report data security issues after digital infrastructure audits in a quarter of their merger and acquisition targets.
The solution lies in a cybersecurity audit as part of the due diligence process, which follows a workflow similar to that outlined in the graphic below.
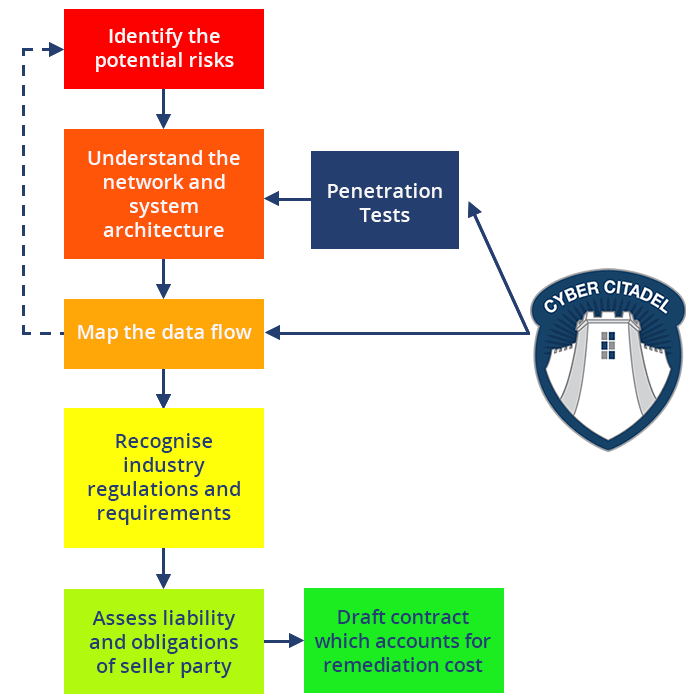
Cybersecurity companies can provide assistance in mergers and acquisitions by joining the due diligence team and a specialist digital risk assessor and to ensure that maximum visibility is delivered across all information technology assets.
A competent cyber security analysis firm should present an ‘eye-opener’ report outlining the state of an organisation’s digital security – including a complete penetration of applications and network infrastructure.
Such a report is designed to indicate areas of risk, saving the acquirer time and reducing the chance of a security issue going undetected. This is especially true if information is hidden within the dark web, or if infrastructure is managed by outdated legacy operating systems – both of which can be difficult to navigate.
Such approaches are called ‘black box tests’ – where the internal structure of a system is unknown – and can be highly revealing of errors and inconsistencies in databases, with relatively little initial information, providing an excellent starting point for digital audits.
Blind black box tests can also be carried out covertly, which adds an advantageous element of discretion to a buyer’s investigation into a business.
As with any financial evaluation, cybersecurity evaluation should be an integral part of the due diligence process to enable maximum opportunity to expose risks, and minimum opportunity for unwanted surprises closer post acquisition.
As with any other findings in due diligence, the results of the cybersecurity evaluation can inform the terms of the transaction or indeed lead to it being aborted.
As an acquirer, business purchasers will be aiming to grow value, not lose it, through a cybersecurity oversight. This is especially true if the acquiring entity is a publicly trading company where the consequences could become public and immediately impact market sentiment towards the business.
So, ensuring a watertight digital fortress is not just about mitigating the cost of remediation, or even ascertaining the right enterprise value, it is also about maintaining the confidence of shareholders, particularly for a publicly listed entity.
Increasing visibility and taking a proactive approach to cybersecurity is a key component of risk assessment in merger and acquisition due diligence. This, in turn, is the key to protecting and building business value.
– Jonathan Sharrock, Cyber Citadel.


